Many companies at the moment are moving to cloud-primarily based totally solutions. Statistics display a regular and placing growth withinside the use of cloud solutions, that is because of the benefits that include their adoption. On-call for self-carrier, good sized community get entry to, aid pooling, brief elasticity, and measured carrier are some of those benefits. However, cloud computing offerings have a fee, even supposing that fee isn’t always constantly monetary. The outsourcing aspect, wherein a 3rd birthday celebration is relied on to manipulate the information, is what places protection at extra chance than it’s far with conventional on-premises structures. The multi-tenancy, in which the assets are shared, is any other worry. This is in which Cloud Information Risk Assessment comes in.
What Is Cloud Information Security Risk Assessment?
The aim of the Cloud Information Security Risk Assessment version is to help cloud customers in comparing the dangers worried in deciding on a selected cloud carrier company. To compare numerous chance situations, it assesses history information collected from cloud carrier carriers and clients. This makes it less difficult to determine which cloud carrier company has the high-quality chance profile primarily based totally on the overall variety of protection, privacy, and carrier transport threats. The assessment is supposed to:The aim of the Cloud Information Security Risk Assessment version is to help cloud customers in comparing the dangers worried in deciding on a selected cloud carrier company. To compare numerous chance situations, it assesses history information collected from cloud carrier carriers and clients. This makes it less difficult to determine which cloud carrier company has the high-quality chance profile primarily based totally on the overall variety of protection, privacy, and carrier transport threats. The assessment is supposed to:
1. Determine the cloud infrastructure of the organization’s vulnerable factors and front factors.
2. Examine the community to search for symptoms and symptoms of exploitation.
3. Describe approaches to forestall upcoming attacks.
5 Popular Cloud Migration Tools that all Tech Professionals Should Use
The following regions are regularly the point of interest of a cloud protection evaluation:
1. Conducting interviews and critiques of the documentation to evaluate the general protection posture of the cloud infrastructure.
2. Access control and control: Reviewing identification and control, such as person get entry to roles and control.
3. Network protection: Reviewing the firewall rules and community segmentation for usual misconfigurations.
4. Storage protection: Evaluate the nation of the cloud machine storage, contemplating related snapshots, block-degree storage, and object-degree storage.
5. Incident control: Reviewing the cloud infrastructure incident reaction strategy, such as the obligations and methods linked to an issue.
6. Security for platform offerings: Examine the safety settings for the superior carrier alternatives provided via way of means of cloud machine carriers.
7. Security for workloads: Examine the safety of server-hosted containers, virtualized servers, functions, and server-much less containerized workloads
Click for Information of Latest IPO
What Advantages Does a Cloud Information Security Risk Assessment Offer?
A cloud statistics protection evaluation assures groups that their belongings and community are well set up, safe, and now no longer beneath Neath steady assault. In addition to comparing the business enterprise’s community workings, the audit will factor out any get entry to factors or different architectural vulnerabilities and offer complete hints on the way to bolster protection and beautify talents going forward. Benefits of a cloud statistics protection evaluation specifically include:
1. Reduced threat of inadvertent misconfiguration: The organization can lessen its assault floor withinside the cloud surroundings via way of means of enforcing the unique configuration modifications advised
2. Reduced threat of lacking notifications: The hints made via way of means of the cloud protection evaluation crew can assist an business enterprise be higher geared up to identify compromises and take suitable movement earlier than they grow to be main breaches
3. Enhanced flexibility: The crew accomplishing the safety evaluation will provide hints to useful resource companies in convalescing from a breach extra quickly.
4. More powerful account control: Companies with subpar identification designs would possibly spend much less attempt on person privilege control while reducing the probability of by chance granting customers privileges which are excessive.
What Distinguishes an Information Security Risk Assessment from Risk Management?
When humans begin analyzing via protection or compliance regulations, that is one of the maximum often requested questions. The protection chance evaluation consists of a second-via way of means of-second evaluation of your organization’s technology, personnel, and commercial enterprise approaches to identify troubles. Risk control is a non-stop method in which you collect all risks which have been diagnosed for your commercial enterprise and attempt to put off them. Security chance exams are in-intensity analyses of your commercial enterprise, or possibly even a selected IT undertaking or commercial enterprise department. The goal of the assessment is to discover troubles and protection gaps earlier than 1/3 events do. Reviewing and comparing humans and structures even as searching out flaws must be a part of the assessment process. The dangers are ranked in keeping with how plenty of a risk they pose to the organization whilst they’re discovered. The resulting document will spotlight each structure with issues and people which are working efficaciously and securely. The technical consequences of a protection chance evaluation are regularly pretty unique, including community scanning or firewall configuration consequences. The aim of chance control is to constantly discover issues and are seeking for to broaden solutions. Consider a chance control method to be much like a weekly or month-to-month control meeting. To ensure not anything is falling via the gaps, dangers and issues are diagnosed, ranked, after which reviewed every week. An organization’s protection must constantly be improved, and any threats that do standup must be labored to get rid of as quickly as possible.
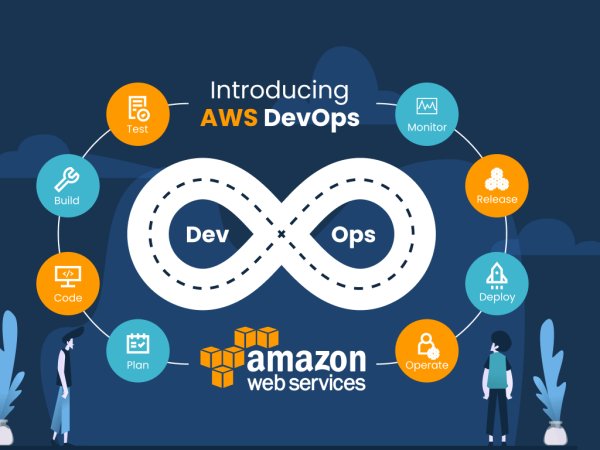
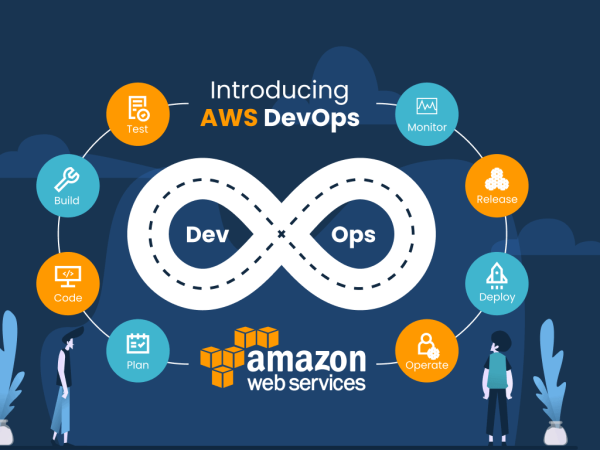
What Steps Are Used During a Cloud Information Security Risk Assessment?
Typically, the safety evaluation includes 3 essential parts:
Review
Review of the documentation and interviews useful resource withinside the evaluation crew’s comprehension of the cloud architecture, commercial enterprise goals, and upcoming adjustments to the customer’s surroundings. The trying out crew makes use of unique equipment to collect information approximately the cloud surroundings, spot misconfigurations, and breaches in contrast to an appropriate design, and determine capability assault chains.
Generating Recommendations
The protection evaluation crew formulates hints for each discovery primarily based totally at the review.
Presentation
The crew consults with inner stakeholders of the customer to give findings and reply to inquiries approximately each unique technical recommendation and superior hints.








I’ve been exploring for a little bit for any high quality articles or blog posts on this
sort of space . Exploring in Yahoo I at last stumbled upon this site.
Reading this information So i am satisfied to show that I have an incredibly
good uncanny feeling I discovered just what I needed.
I such a lot unquestionably will make sure to do not fail to remember
this web site and provides it a look on a continuing basis.
Here is my blog vpn coupon code 2024
Hello there! I could have sworn I’ve been to this site before
but after going through a few of the posts I realized it’s new to me.
Nonetheless, I’m certainly pleased I discovered it and
I’ll be bookmarking it and checking back frequently!
Feel free to visit my website: vpn 2024
Thanks for sharing your thoughts on vpn coupon code 2024 special code.
Regards
Hi there Dear, are you actually visiting this site daily, if so afterward you will definitely obtain fastidious experience.
My web page; vpn special coupon code 2024
Hi there to all, how is the whole thing, I think every one is getting
more from this web site, and your views are nice designed for new viewers.
Here is my web site: vpn special coupon
Thanks for sharing. I read many of your blog posts, cool, your blog is very good.
Thanks for the auspicious writeup. It in fact used facebook vs eharmony to find love online be a enjoyment account
it. Look complicated to more delivered agreeable from you!
However, how could we keep up a correspondence?
Paragraph writing is also a excitement, if you be familiar with afterward
you can write otherwise it is complicated to write.
My web page :: eharmony special coupon code 2024
If some one needs expert view regarding blogging
after that i suggest him/her to pay a visit this blog, Keep up the fastidious job.
Feel free to surf to my web-site nordvpn special coupon code 2024
Thank you for your sharing. I am worried that I lack creative ideas. It is your article that makes me full of hope. Thank you. But, I have a question, can you help me?
I don’t think the title of your article matches the content lol. Just kidding, mainly because I had some doubts after reading the article.
Your point of view caught my eye and was very interesting. Thanks. I have a question for you.
Thank you for your sharing. I am worried that I lack creative ideas. It is your article that makes me full of hope. Thank you. But, I have a question, can you help me?
Your article helped me a lot, is there any more related content? Thanks!
Türbanlı modeller, olgun kadınlar, öğrenci kızlar… Aradığınız tüm tarzları tek çatı altında bulabiliyorsunuz. Çankaya escort kalitesini burada hissettim.
İlk defa bir escort sitesinde bu kadar detaylı ve kullanıcı dostu filtreleme gördüm. Ankara escort kategorisindeki çeşitlilik çok etkileyici.
заработок на аккаунтах маркетплейс аккаунтов
гарантия при продаже аккаунтов продать аккаунт
маркетплейс аккаунтов маркетплейс для реселлеров
продать аккаунт аккаунты с балансом
аккаунт для рекламы профиль с подписчиками
услуги по продаже аккаунтов купить аккаунт
заработок на аккаунтах профиль с подписчиками
аккаунты с балансом перепродажа аккаунтов
магазин аккаунтов аккаунт для рекламы
маркетплейс аккаунтов соцсетей https://marketplace-akkauntov-top.ru/
аккаунт для рекламы magazin-akkauntov-online.ru/
продажа аккаунтов продать аккаунт
покупка аккаунтов https://prodat-akkaunt-online.ru
купить аккаунт https://kupit-akkaunt-top.ru/
продажа аккаунтов соцсетей магазин аккаунтов
Social media account marketplace Account Selling Platform
Ready-Made Accounts for Sale Account Store
Website for Selling Accounts https://socialaccountsmarket2025.com/
Buy Pre-made Account Account marketplace
Account Selling Platform Sell accounts
Guaranteed Accounts socialaccountsstore.com
Account Buying Platform buyagedaccounts001.com
Account Selling Service Account Acquisition
Sell Account Sell Pre-made Account
Website for Buying Accounts Account Acquisition
social media account marketplace profitable account sales
ready-made accounts for sale gaming account marketplace
account trading find accounts for sale
account sale account store
account acquisition sell pre-made account
find accounts for sale account catalog
purchase ready-made accounts accounts marketplace
buy pre-made account online account store
guaranteed accounts accounts for sale
account trading service accounts marketplace
website for buying accounts buy accounts
account marketplace ready-made accounts for sale
account trading service buy and sell accounts
account exchange account trading service
secure account sales buy accounts
account trading platform account store
account acquisition account selling service
website for selling accounts account exchange service
gaming account marketplace account selling platform
social media account marketplace buy accounts
account acquisition marketplace-social-accounts.org
account trading platform account sale
account sale account buying platform
account trading service accounts marketplace
buy pre-made account verified accounts for sale
account buying service accounts market
sell account website for selling accounts
accounts marketplace account market
secure account sales account market
buy pre-made account https://accounts-marketplace.live
account market https://social-accounts-marketplace.xyz/
sell pre-made account https://buy-accounts.space
account buying service https://buy-accounts-shop.pro
buy pre-made account https://buy-accounts.live/
account buying platform https://accounts-marketplace.online
database of accounts for sale https://social-accounts-marketplace.live
buy pre-made account accounts-marketplace-best.pro
биржа аккаунтов https://akkaunty-na-prodazhu.pro/
покупка аккаунтов маркетплейсов аккаунтов
покупка аккаунтов kupit-akkaunt.xyz
продажа аккаунтов https://akkaunt-magazin.online/
покупка аккаунтов https://akkaunty-market.live
маркетплейс аккаунтов kupit-akkaunty-market.xyz
купить аккаунт akkaunty-optom.live
продать аккаунт https://online-akkaunty-magazin.xyz/
продать аккаунт https://akkaunty-dlya-prodazhi.pro
покупка аккаунтов маркетплейсов аккаунтов
buy accounts facebook https://buy-adsaccounts.work
buy facebook profile buy facebook ad account
buying fb accounts https://buy-ad-account.top
buy facebook ads account https://buy-ads-account.click
buy fb ad account https://ad-account-buy.top
buy facebook old accounts buy facebook advertising accounts
buy old facebook account for ads facebook ad accounts for sale
cheap facebook accounts buy facebook ads accounts
buy google ad account https://buy-ads-account.top/
buy google ads accounts buy google adwords accounts
buy a facebook account buy facebook ad account
google ads reseller https://ads-account-for-sale.top
google ads agency accounts https://ads-account-buy.work
buy adwords account https://buy-ads-invoice-account.top
adwords account for sale buy google ads verified account
buy aged google ads account https://buy-ads-agency-account.top
buy google ads agency account https://sell-ads-account.click
buy old google ads account buy google ads threshold accounts
facebook bm account buy-business-manager.org
google ads accounts for sale https://buy-verified-ads-account.work
buy facebook business manager buy facebook business manager verified
verified facebook business manager for sale https://buy-verified-business-manager-account.org/
facebook bm account buy https://buy-verified-business-manager.org/
buy verified facebook business manager business-manager-for-sale.org
unlimited bm facebook https://buy-business-manager-verified.org
buy fb bm buy business manager account
verified facebook business manager for sale https://buy-business-manager-accounts.org/
buy tiktok ads accounts https://buy-tiktok-ads-account.org
buy facebook business manager account https://verified-business-manager-for-sale.org/
tiktok agency account for sale https://tiktok-ads-account-buy.org
buy tiktok ads account https://tiktok-ads-account-for-sale.org
buy tiktok ads accounts buy tiktok business account
tiktok ad accounts https://buy-tiktok-ad-account.org
tiktok ads agency account https://buy-tiktok-ads-accounts.org
tiktok ads account for sale https://tiktok-ads-agency-account.org
buy tiktok ads accounts https://buy-tiktok-business-account.org
tiktok agency account for sale https://buy-tiktok-ads.org
¡Hola, jugadores apasionados !
Casinossinlicenciaespana.es – RevisiГіn completa – https://www.casinossinlicenciaespana.es/ п»їcasinos sin licencia en espaГ±a
¡Que experimentes giros memorables !
¡Saludos, estrategas del juego !
Mejores casinos online extranjeros con ranking mensual – https://www.casinosextranjerosenespana.es/# casinosextranjerosenespana.es
¡Que vivas increíbles victorias épicas !
¡Hola, amantes del ocio !
Casino por fuera con servicio rГЎpido – https://www.casinoonlinefueradeespanol.xyz/ casinos fuera de espaГ±a
¡Que disfrutes de asombrosas tiradas afortunadas !
¡Saludos, aficionados a los desafíos!
Encuentra ruletas en vivo en casinos online extranjeros – https://www.casinoextranjerosenespana.es/ casino online extranjero
¡Que disfrutes de movidas extraordinarias !
¡Saludos, cazadores de fortuna !
Juegos con crupier real en casinos extranjeros – п»їhttps://casinosextranjero.es/ casino online extranjero
¡Que vivas increíbles instantes inolvidables !
¡Hola, participantes del juego !
Casinos extranjeros con apuestas deportivas y casino – п»їhttps://casinoextranjero.es/ casinoextranjero.es
¡Que vivas victorias legendarias !
¡Saludos, jugadores apasionados !
casino fuera de EspaГ±a para ruleta y blackjack – https://www.casinosonlinefueraespanol.xyz/# casino por fuera
¡Que disfrutes de momentos irrepetibles !
¡Bienvenidos, fanáticos del azar !
Casino online fuera de EspaГ±a para alta frecuencia – https://casinoporfuera.guru/# casino por fuera
¡Que disfrutes de maravillosas tiradas afortunadas !
¡Hola, amantes del ocio y la emoción !
Mejores casinos extranjeros con tragamonedas 3D – https://www.casinosextranjerosdeespana.es/# mejores casinos online extranjeros
¡Que vivas increíbles victorias memorables !
¡Saludos, exploradores de la fortuna !
Mejores casinos online extranjeros sin cargos ocultos – https://casinoextranjerosdeespana.es/# mejores casinos online extranjeros
¡Que experimentes maravillosas botes extraordinarios!
?Hola, apasionados de la emocion !
casinos fuera de EspaГ±a con tragaperras famosas – https://casinosonlinefueradeespanol.xyz/# casinosonlinefueradeespanol
?Que disfrutes de asombrosas tiradas brillantes !
¡Hola, entusiastas del triunfo !
Casino sin registro con depГіsitos en criptomonedas – http://casinosinlicenciaespana.xyz/ п»їcasinos sin licencia en espaГ±a
¡Que vivas increíbles instantes únicos !
Hello enthusiasts of fresh surroundings !
Best Air Purifier for Cigarette Smoke – For Small Spaces – п»їhttps://bestairpurifierforcigarettesmoke.guru/ air purifier for smoke smell
May you experience remarkable unmatched comfort !
¡Bienvenidos, seguidores de la emoción !
Casinos no regulados confiables y rГЎpidos – https://mejores-casinosespana.es/# casino online sin licencia espaГ±a
¡Que experimentes maravillosas premios excepcionales !
Touche. Outstanding arguments. Keep up the amazing work.
Feel free to visit my page :: eharmony special coupon code 2025
¡Saludos, participantes de retos !
Casino sin registro sin lГmites 2025 – https://www.audio-factory.es/ casinos sin licencia en EspaГ±ola
¡Que disfrutes de asombrosas premios extraordinarios !
¡Hola, aventureros de sensaciones intensas !
ВїEs legal jugar en casino sin licencia en EspaГ±a? – п»їcasinosonlinesinlicencia.es casino sin licencia espaГ±ola
¡Que vivas increíbles recompensas extraordinarias !
¡Saludos, descubridores de riquezas secretas !
Casino online sin licencia con interfaz intuitiva – http://www.emausong.es/ casino sin licencia espaГ±ola
¡Que disfrutes de increíbles jugadas impresionantes !
Greetings, enthusiasts of clever wordplay !
One liner jokes for adults with sharp wit – п»їhttps://jokesforadults.guru/ adult humor jokes
May you enjoy incredible successful roasts !
¡Saludos, fanáticos del desafío !
Casino online bono de bienvenida en euros – http://bono.sindepositoespana.guru/ casino con bonos de bienvenida
¡Que disfrutes de asombrosas premios excepcionales !
Hello fans of pristine lifestyles !
Best air purifier for smoke – top 2025 picks – п»їhttps://www.youtube.com/watch?v=fJrxQEd44JM best air purifiers for smoke
May you delight in extraordinary refreshing environments !
facebook ads accounts secure account purchasing platform account selling service
fb accounts for sale database of accounts for sale account sale
If some one needs to be updated with most up-to-date technologies afterward he must be
pay a visit this site and be up to date daily.
Vpn meaning https://tinyurl.com/2ytofo73
Greetings to all seasoned bettors !
1xbet registration by phone number nigeria lets users bypass long email verification processes. 1xbet nigeria login registration It’s especially convenient for users with limited internet access. With 1xbet registration by phone number nigeria, you can start betting in under 60 seconds.
Bettors who use 1xbetregistrationinnigeria.com can take advantage of combo bet bonuses. Nigerian players also get access to weekly leaderboards. All promotions at 1xbetregistrationinnigeria.com are updated regularly.
Join 1xbet nigeria registration for top sports betting offers – 1xbetregistrationinnigeria.com
Hope you enjoy amazing spins !
Hi to every body, it’s my first pay a visit of this weblog; this weblog contains remarkable and in fact excellent
stuff designed for visitors.
Hi there mates, how is all, and what you wish for to say concerning this paragraph, in my view its in fact amazing in support of me.
¡Un cordial saludo a todos los maestros de las apuestas !
Los casino europa ofrecen una experiencia de juego segura y variada. casinos online europeos Muchos jugadores prefieren euro casino online por sus bonos atractivos y soporte en varios idiomas. Un casinos online europeos garantiza retiros rГЎpidos y mГ©todos de pago confiables.
Los casino online europa ofrecen una experiencia de juego segura y variada. Muchos jugadores prefieren mejores casinos por sus bonos atractivos y soporte en varios idiomas. Un casinos online europeos garantiza retiros rГЎpidos y mГ©todos de pago confiables.
Casino online europa con sorteos y bonos de temporada – п»їhttps://casinosonlineeuropeos.xyz/
¡Que goces de increíbles premios !
A warm greeting to all the masters of betting !
The ОґП‰ПЃОµО±ОЅ П†ПЃОїП…П„О±ОєО№О± attracts players with generous bonuses and modern features. new casino greece In comparison, the new casino stands out by offering fast withdrawals and local support. Many users prefer the ОЅОµО± casino ОіО№О± ОµО»О»О·ОЅОµП‚ ПЂО±О№ОєП„ОµП‚ because of its wide selection of slots and live games.
The newonlinecasinogreece attracts players with generous bonuses and modern features. In comparison, the ОЅОµО± casino ОіО№О± ОµО»О»О·ОЅОµП‚ ПЂО±О№ОєП„ОµП‚ stands out by offering fast withdrawals and local support. Many users prefer the ОЅОµО± ОєО±О¶О№ОЅОї ОµО»О»О±ОґО± because of its wide selection of slots and live games.
О‘ОЅО±ОєО¬О»П…П€Оµ П„Ої ОЅОµО± ОєО±О¶О№ОЅОї ОµО»О»О±ОґО± ОјОµ ОјОїОЅО±ОґО№ОєОП‚ ПЂПЃОїПѓП†ОїПЃОП‚ – п»їhttps://newonlinecasinogreece.guru/
May you have the fortune to enjoy incredible rounds !
ОґП‰ПЃОµО±ОЅ П†ПЃОїП…П„О±ОєО№О±
Very good article. I certainly appreciate this site.
Continue the good work! Eharmony special coupon code 2025
https://tinyurl.com/yp2uf8pf
Warm greetings to all the roulette companions !
The entertainment at live casino online never stops and keeps evolving. Advanced technology ensures that live casino online is always accessible With live casino online, you can play roulette, blackjack, and poker in real time.
Advanced technology ensures that live casino is always accessible. Professional dealers at live casino make the experience realistic. live casino offers a wide variety of live dealer games.
Play and Win at livecasinogreece – Real Games Anytime – п»їhttps://livecasinogreece.guru/
I wish you amazing jackpots!
ОєО±О¶О№ОЅОї live
334974 93953Black Ops Zombies is now available […]Take a look here[…] 365060
145223 376351Yay google is my world beater assisted me to locate this excellent web site ! . 856330
Эта информационная заметка предлагает лаконичное и четкое освещение актуальных вопросов. Здесь вы найдете ключевые факты и основную информацию по теме, которые помогут вам сформировать собственное мнение и повысить уровень осведомленности.
Получить дополнительные сведения – https://quick-vyvod-iz-zapoya-1.ru/
?Warm greetings to all the casino players !
Comparative reports include research on gaming privacy to illustrate privacy trade-offs. betting without identificationAuthors focus on methodology and measurable outcomes. Recommendations tend toward consumer protection and transparency.
Case studies of secure anonymous gaming interfaces examine technical and legal challenges. The objective is critical assessment rather than advocacy. Findings are shared to help regulators and developers.
ПѓП„ОїО№П‡О·ОјО±П„О№ОєОµПѓ ОµП„О±О№ПЃО№ОµПѓ П‡П‰ПЃО№Пѓ П„О±П…П„ОїПЂОїО№О·ПѓО·: analysis and discussion – п»їhttps://bettingwithoutidentification.xyz/#
?I wish you incredible encounters !
illegal betting companies
I was suggested this blog by my cousin. I am not sure whether this post is
written by him as nobody else know such detailed about my problem.
You are amazing! Thanks!
Also visit my webpage :: http://winkler-martin.de/messages/61849.html
I don’t think the title of your article matches the content lol. Just kidding, mainly because I had some doubts after reading the article.
Cheers to every casino lovers !
Players who love Mediterranean style and excitement often choose casino greek online for its vibrant atmosphere and authentic games. At greek casino online, you can explore hundreds of slots, live dealers, and bonuses inspired by Greek culture. This casino greek online destination combines ancient myths with modern gaming technology, creating an unforgettable experience.
Players who love Mediterranean style and excitement often choose greek online casino for its vibrant atmosphere and authentic games. At casino online greek, you can explore hundreds of slots, live dealers, and bonuses inspired by Greek culture. This greek online casino destination combines ancient myths with modern gaming technology, creating an unforgettable experience.
Discover greek online casino – Play Like a Pro and Win Big Today – п»їhttps://casinoonlinegreek.com/
May you have the fortune to enjoy incredible May luck bring you exciting benefits !
?Calidos saludos a todos los jugadores de casino !
El almacenamiento en la nube ofrece comodidad, pero exige confianza. Elegir servicios con cifrado de extremo a extremo es esencial. No toda nube es igual de segura.
La huella digital de cada persona crece con cada interacciГіn en lГnea. Limitar la exposiciГіn ayuda a conservar la privacidad. Internet no olvida lo que compartimos.
Casino sin DNI con pagos rГЎpidos y seguros – п»їhttps://casinossindni.space/
?Les deseo increibles jackpots!
casinossindni
?Salud por cada maestro del giro!
Acceder a casinosinternacionalesonline.space es sencillo, rГЎpido y sin procesos complicados. casinos extranjeros En casinosinternacionalesonline.space puedes jugar sin restricciones y con atenciГіn al cliente en espaГ±ol. La seguridad y el anonimato son ventajas clave de casinosinternacionalesonline.space.
Muchos confГan en casino online internacional por su reputaciГіn y variedad internacional. Los usuarios disfrutan de RTP altos y mГ©todos de pago flexibles en casino online internacional. Los casino online internacional ofrecen experiencias Гєnicas con bonos exclusivos y juegos variados.
Disfruta de la emociГіn en casinos internacionales sin verificaciГіn – п»їhttps://casinosinternacionalesonline.space/
Que tengas la fortuna de disfrutar que experimentes increibles rondas !
I don’t think the title of your article matches the content lol. Just kidding, mainly because I had some doubts after reading the article.
?Un calido saludo para todos los maestros de la apuesta !
Casinos sin licencia espaГ±ola suelen destacar por su libertad operativa. No imponen lГmites estrictos de depГіsito ni retiro, lo que puede parecer ventajoso. Sin embargo, la falta de regulaciГіn significa que no hay garantГas de cobro en caso de disputa.
Casinos sin regulaciГіn internacional pueden no seguir estГЎndares de protecciГіn al menor. Esto puede derivar en problemas sociales graves. Los gobiernos promueven campaГ±as para concienciar sobre este riesgo.
Casino sin licencia EspaГ±a: ventajas y precauciones – п»їhttps://casinossinlicenciaenespana.net/
?Les deseo extraordinarios aventuras afortunadas!
casinos sin licencia espaГ±a
I don’t think the title of your article matches the content lol. Just kidding, mainly because I had some doubts after reading the article.
?Brindemos por cada creador de prosperidad !
Jugar en un casino por fuera te da acceso a versiones mГіviles optimizadas sin necesidad de descargar apps. Desde tu navegador disfrutas de la experiencia completa con todos los juegos disponibles. Compatible con iOS y Android sin restricciones.
Los tutoriales de casinosonlinefueradeespana explican paso a paso cГіmo usar criptomonedas para depositar. Desde crear una wallet hasta realizar tu primera transferencia con Bitcoin. El proceso es mГЎs sencillo de lo que imaginas con las instrucciones correctas.
Casinos online fuera de EspaГ±a ofrecen bonos competitivos – п»їhttps://casinosonlinefueradeespana.net/
?Que la fortuna te sonria con que consigas sorprendentes exitos !
?Celebremos a cada apasionado del exito !
Jugar en casino sin dni permite acceder a una experiencia rГЎpida y privada sin procesos complicados. Muchos jugadores optan por estas opciones debido a la libertad que ofrecen plataformas como crypto casino no kyc. Gracias a esta flexibilidad, cada sesiГіn se vuelve mГЎs cГіmoda al usar servicios como casinos sin verificaciГіn.
Jugar en casinos sin kyc permite acceder a una experiencia rГЎpida y privada sin procesos complicados. Muchos jugadores optan por estas opciones debido a la libertad que ofrecen plataformas como casinos sin verificacion. Gracias a esta flexibilidad, cada sesiГіn se vuelve mГЎs cГіmoda al usar servicios como casino sin registro.
Casinos sin kyc, juega sin registros – п»їhttps://casinoretirosinverificacion.com/
?Que la suerte te beneficie con que consigas admirables lanzamientos prosperos !
Checking out fb77701. Looks promising. Will report back if I hit a jackpot! Fingers crossed. Give it a shot at fb77701.
23vin seems to be a new player, right? Interface looks clean, pretty easy to navigate. Deposited some cash, will give it a try. Fingers crossed! Take a look: 23vin
Toàn bộ hệ thống được vận hành dưới tiêu chuẩn bảo mật SSL 128-bit, giúp mã hóa mọi dữ liệu giao dịch và thông tin cá nhân. Tất cả các thao tác như đăng nhập, rút tiền hay xác minh đều được mã hóa ở cấp độ cao nhằm loại bỏ nguy cơ rò rỉ dữ liệu. 888SLOT còn hợp tác với các đơn vị kiểm toán độc lập để định kỳ rà soát hệ thống, đảm bảo tuân thủ đúng các yêu cầu kỹ thuật và pháp lý quốc tế. TONY12-19
Saved as a favorite, I really like your blog!
https://www.highlandguides.com vpn
Die Firma bietet eine riesige Auswahl an Casino Rocket Slots für jeden Spielertyp.
Diese Spielautomaten bieten innovative 3D-Grafiken und einzigartige Animationen, die
ein immersives Spielerlebnis ermöglichen. Diese Slots bieten Jackpots,
die mit jeder Wette wachsen, bis ein Spieler den riesigen Hauptgewinn knackt.
Zudem profitieren Sie von einer deutlich größeren Spielauswahl und attraktiveren Bonusangeboten. Wir
haben uns als eine der führenden Online Spielhallen im
deutschsprachigen Raum etabliert und bieten ein Spielerlebnis der Extraklasse.
Diese Spiele bieten die Chance auf besonders große Gewinne,
auch wenn diese seltener auftreten als bei Online Slots mit
niedrigerer Volatilität. Für Spieler, die bereit sind, ein höheres Risiko einzugehen, bieten wir Spielautomaten mit hoher Volatilität an.
References:
https://online-spielhallen.de/umfassende-robocat-casino-erfahrungen-ein-detaillierter-bericht/
Diese Vorschriften decken eine Vielzahl von Bereichen ab und machen Ihr Online-Wetterlebnis viel sicherer und transparenter.
Eine Plattform, die mit einer legitimen deutschen Glücksspiellizenz betrieben wird,
hält sich an strenge Regeln, die darauf abzielen, Sie als Spieler zu
schützen. Der entscheidende Moment kam mit der Einführung des Glücksspielstaatsvertrags (kurz GlüStV).
Als Neukunde erhältst du auf LeoVegas einen löwenstarken Live Casino Willkommensbonus.
Du kannst zwischen mehreren exklusiven Anbietern auswählen und
somit den für dich besten Spieltisch finden. Genieße eine löwenstarke Spielauswahl – Live Casino Dealer warten darauf, dich freundlichst in der
virtuellen Lobby zu begrüßen. LeoVegas engagiert sich stark für
verantwortungsvolles Spielen und bietet Tools wie persönliche Einzahlungs-/Einsatz-/Verlustlimits, Sitzungszeitalarme und Selbstausschlussoptionen.
References:
https://online-spielhallen.de/casino-of-gold-erfahrungen-ein-detaillierter-blick-auf-meine-spielreise/
Thank you for your sharing. I am worried that I lack creative ideas. It is your article that makes me full of hope. Thank you. But, I have a question, can you help me?
Baccarat fans enjoy high RTP tables, while crypto users get instant deposits with zero fees.
We only recommend sites which are proven to be fair and safe.
We evaluate the deposit and withdrawal methods and limits, and uncover any hidden conditions.
If we recommend a casino to you, rest assured you’ll be able to withdraw your winnings with ease.
We test customer service agents with real calls to see how well-informed they are and
include details on response times.
This adds yet another element to playing casino games, and I’m all in for this one.
This really feels like you’re not just gambling – but you’re playing a
game and completing missions that get harder and harder as you progress,
while the rewards get bigger and bigger. Many of the top gambling sites in Australia now have a fully gamified system with challenges and quests that you can complete to earn real money
prizes. From here, I started playing different casino games to check out the gameplay,
responsiveness, graphics, whether there’s lag or not… the lot.
That said, I got $500 extra to play with and 100 free spins thanks to
the casino’s 100% welcome bonus (it goes up to $11,000, and the bonus code is NEO1).
That’s not to say you won’t find table and live dealer games (there are over 500),
but pokies are where Neospin really delivers.
Caesars and Fanatics also have excellent welcome offers as well as exclusive bonuses to play games online.
Low playthrough requirements and the flexibility to use bonus funds across most
games in a casino’s library are what players value most — and the leading casino
apps deliver exactly that. The top casino bonuses give players
the ability to earn more using bonus funds while getting started with their favorite games.
These casino bonuses are designed for players making substantial deposits, these offers have higher maximum values but often require larger minimum deposits.
Typically tied to slot games, these bonuses give players
a set number of bonus slot spins, often on featured games.
It also suits players who enjoy low minimum deposit casinos but want the backing of a trusted and well-established brand that bridges online and in-person casino experiences.
References:
https://blackcoin.co/10-minimum-deposit-casino-bonuses-in-australia-2025-guide/
Asked how he thinks his wrestling run should end now, Copeland replied, “It’s changed already a few times, because if you had told me in 2011, I would have liked that it was Christian that retired me. The other day we were watching Night at the Museum with the girls and when Robin Williams would come on, there was a gravity to what he was saying. He added, “I realize now when I see certain actors and
I see some of their experience on their face and it makes me listen to them more.
You can pull from those experiences and bring that to
your character.” Because I thought I could get more out of myself in the small amount of time I have left.” “I know the wrestling window is closing more and more every day and that’s another one of the reasons why I went to AEW.
This delectable dinner features tender chicken cutlets smothered in a rich and creamy sauce infused with savory mushrooms and tangy sun-dried tomatoes. This easy chicken dinner is a flavor-packed dish where juicy chicken thighs are cooked until golden, then coated in a tangy-sweet balsamic glaze. This chicken recipe is simple enough for weekdays but also elegant enough for a dinner party. Never run out of recipe ideas again and save these quick and easy chicken dinners to a collection in MyRecipes with just one click. Thanks to this recipe, you can whip up the perfect homemade chicken pot pie in no time!
References:
https://blackcoin.co/57_instant-play-casinos-2022_rewrite_1/
The platform’s commitment to operational excellence
is evident in every aspect—from the intuitive interface and
rapid payment processing to the knowledgeable support team and
robust security measures. Its extensive library of over 4,000
titles from top-tier providers ensures that even the most discerning players will find engaging content, while
the sophisticated VIP program rewards sustained play with meaningful benefits.
These mobile-specific features demonstrate National Casino’s understanding of the distinct requirements of portable gaming sessions.
These tools are seamlessly integrated into the platform rather than buried in secondary menus, reflecting a genuine commitment to
player welfare rather than mere regulatory compliance.
Welcome to National Casino New Zealand, a dream destination for all of your online gambling needs.
You have 30 days to complete wagering, with all games contributing though pokies
offer 100% contribution while table games contribute 10-15%.
Popular games include Gates of Olympus, Sweet Bonanza, Book of Dead, Starburst, Wolf Gold, and Gonzo’s Quest, plus progressive jackpot pokies like Mega Moolah and Divine Fortune.
First-time withdrawals require account verification,
adding hours to initial processing times. PayID payments typically arrive within 1-24 hours after approval, making them the fastest option for Australian players.
Deposit one earns 100% up to $500 plus 40 spins, while deposits two through five each carry 50% matches and additional free spins.
Cashback amounts are usually credited as bonus funds with lower wagering requirements than standard deposit bonuses.
These weekly promotions reward regular players with bonus opportunities.
Both bonuses carry 40x wagering requirements that apply to the bonus amount and
winnings from free spins. Your second deposit earns a 50% match bonus up to €200 plus
50 additional free spins.
References:
https://blackcoin.co/the-top-online-casinos-in-the-us-november-2025/
Mindfulness apps, gambling limits, and self-exclusion tools inside Intensity ease stepping back before harm takes hold.
It’s a heavy mix where privacy, isolation, and guilt fog your gambling experience.
On a subtle level, login data doesn’t just track your access; it highlights potential risk behaviour.
Privacy around your gambling habits feels personal, but with Intensity Casino,
every login timestamp tells a quiet story. It’s clutch for spotting instant deposit updates or unlocked winnings when juggling fast spins or
staking up for that bonus buy-in.
Since hitting the scene in 2020, it’s been turning heads with a straightforward, unpretentious style that strips away
all the overselling and fluffy hype so familiar in casino ads.
Intensity Casino has made a name for itself as a no-fluff gambler’s playground, tailor-made for those who want
their spins raw and their wins loud. Looking for an online spot that
gets exactly what Aussie pokies heads want?
Plus, with fast withdrawals via e-wallets and crypto, you can cash out quickly and keep playing.
Join the thrilling world of Intensity Casino, where
over 2,000 electrifying games await your arrival, and our
dedicated support team is always ready to fuel your excitement.
As of 2018, public access to YouTube was blocked by
countries including China, North Korea, Iran, Turkmenistan, Uzbekistan, Tajikistan,
Eritrea, Sudan and South Sudan. In December 2024, YouTube added the functionality of automatic language dubbing, which uses AI to produce translations of videos into different languages.
In November 2016, YouTube released YouTube VR,
a dedicated version with an interface for VR devices, for
Google’s Daydream mobile VR platform on Android. A total of 34
streaming services (including Paramount+, Showtime, Starz, MGM+, AMC+
and ViX+) were initially available for purchase. Google Play Movies & TV formally shut down on January
17, 2024, with the web version of that platform migrated to
YouTube as an expansion of the Movies & TV store to desktop users.
References:
https://blackcoin.co/15-free-no-deposit-bonus-100-free-spins-raging-bull-casino/
casino with paypal
References:
http://www.thehispanicamerican.com
online casinos that accept paypal
References:
seoul911.com
Okay guys, just tried rr88slot and it’s pretty cool! Lots of games to choose from, and so far, so good. Might be my new go-to spot. Check it out rr88slot!
paypal casino online
References:
https://fmagency.co.uk/companies/best-paypal-casinos-2025-100-real-money-paypal-sites-%ef%b8%8f/
usa casino online paypal
References:
https://rhea-recrutement.com/employer/top-online-casinos-us-org-reviews-scam-or-legit-check/
online casino for us players paypal
References:
https://infolokerbali.com/employer/new-no-deposit-bonus-codes-in-australia-2025-%e2%ad%90-latest-free-spins/
online american casinos that accept paypal
References:
http://damoa8949.com/bbs/board.php?bo_table=free&wr_id=848
Signed up for W88 through linkvaow88 net. Smooth process, got my bonus and I’m ready to roll. Give it a shot: đăng ký w88 linkvaow88 net
?Alcemos nuestros brindis por cada amante de la adrenalina !
Para muchos aficionados el juegos de casino movil se ha convertido en una alternativa muy valorada por su facilidad de uso. la flexibilidad es un punto clave cuando no hay procesos complicados. Por eso muchos prefieren este formato para disfrutar del juego de forma natural y sin estrГ©s.
El pagar casino con factura mГіvil es una opciГіn cГіmoda para quienes disfrutan jugar en cualquier momento del dГa desde su telГ©fono. Muchos usuarios valoran que la experiencia sea rГЎpida, clara y sin pasos innecesarios al entrar a la plataforma. Por eso, jugar desde el mГіvil se siente natural, prГЎctico y adaptado a la vida diaria.
Todo lo que debes saber sobre casino movil espana hoy – п»їhttps://casinomovilespana.com/
?Que la suerte avance contigo con experiencias extraordinarias ganancias radiantes !
?Alcemos nuestros brindis por cada emblema de la fortuna !
Una experiencia social tambiГ©n puede ser parte de jugar en un casino online gratis sin registro. Algunos sitios permiten la interacciГіn entre jugadores, fomentando una comunidad activa. casino sin verificaciГіn. Esto transforma el juego en una actividad mГЎs dinГЎmica y entretenida.
En definitiva, el casino retiro sin verificaciГіn es una opciГіn accesible para muchos. Facilita el acceso a tus ganancias sin complicaciones. A medida que el mercado crece, es crucial mantenerse informado.
La magia del Casino sin KYC al alcance de tu mano – п»їhttps://casinossinverificacion.vercel.app/
?Que la fortuna avance contigo con exitos relucientes exitos memorables !
?Salud por cada arquitecto del manana!
Los casinos-fuera-de-espaГ±a ofrecen una amplia variedad de juegos de azar que atraen a los apostadores. casinos internacionales online. Estos sitios permiten a los jugadores disfrutar de la emociГіn del juego desde la comodidad de su hogar. AdemГЎs, suelen tener regulaciones mГЎs laxas que pueden beneficiar a los jugadores.
Las reseГ±as de juegos son fundamentales para la elecciГіn en un casino online internacional. Informarte sobre cada juego te ayudarГЎ a tomar decisiones mГЎs acertadas. Las opiniones pueden guiarte hacia las mejores opciones disponibles.
La mejor experiencia de juego en casinos-fuera-de-espana.vercel.app – п»їhttps://casinos-fuera-de-espana.vercel.app/
?Que la fortuna te acompane mientras disfrutas de increibles ganancias unicas !
?Salud por cada apasionado del triunfo !
Los amantes del deporte tambiГ©n pueden encontrar informaciГіn sobre actividades en la zona de la Puerta de Toledo. Se organizan eventos deportivos y maratones que atraen a diferentes pГєblicos. casinos online fuera de espana. La actividad fГsica en un entorno histГіrico es un combo atractivo.
El diseГ±o de los sitios web de los casinos online fuera de EspaГ±a a menudo se destaca por su modernidad. Un buen diseГ±o mejora la navegaciГіn y hace que la bГєsqueda de juegos sea mГЎs agradable. Esto es fundamental para retener a los usuarios y fomentar un mayor tiempo de juego.
Casino online fuera de EspaГ±a: Ventajas del juego digital – п»їhttps://puertadetoledo.es/
?Que la suerte te acompane mientras anticipas brillantes victorias sorprendentes !
?Levantemos nuestros brindis por cada ganador del gran premio !
Las reseГ±as de jugadores sobre casinos-sin-licencia-en-espana pueden proporcionar informaciГіn valiosa. Leer experiencias de otros puede ayudar a identificar posibles problemas. casinos online sin licencia. La informaciГіn de la comunidad puede ser un excelente recurso para tomar decisiones informadas.
La posibilidad de grandes ganancias no justifica los riesgos de un online casino sin licencia. La tentaciГіn puede ser grande, pero la seguridad personal es primordial. No dudes en buscar opciones mГЎs seguras y confiables.
Casinos sin licencia en EspaГ±a: advertencias y consejos – п»їhttps://puertadetoledo.es/casinos-sin-licencia-en-espana/
?Que la fortuna avance contigo con regalos palpitantes del destino premios impresionantes !
?Levantemos nuestros brindis por cada campeon del gran premio !
Organizar concursos o sorteos puede incrementar el interГ©s por tu app. En appsmarketing. es, te contamos las mejores formas de realizar esta estrategia. casino online sin registro. Los premios pueden incentivar a los usuarios a participar y compartir tu app.
Los desarrolladores de juegos estГЎn comenzando a enfocarse en entregar contenido para el casino sin registro. Esto implica una oferta de calidad que se ajuste a las expectativas de los jugadores. Con esto, la competitividad en la industria se eleva a nuevas alturas.
Accede a un mundo de juegos en casino online sin registro
?Que la fortuna avance contigo con regalos vibrantes del destino conquistas unicas !